As federal organizations continue building services on cloud providers and deploying to container orchestration platforms, virtual servers, or physical hardware, securing access to cloud resources is crucial. There are two common methods for access control: RBAC (Role-Based Access Control) and access keys. You know, those keys need to be rotated every six months or whatever the cadence is. That process can be automated but is painful, and if not done properly, it can lead to an incident. Depending on the number of keys, it can become burdensome and painful for teams. As noted by Zscalar, 28 percent of access was through keys instead of roles or groups within AWS. Can we use RBAC to mitigate these pain points?
RBAC works similarly to Access Keys in the sense that it generates session tokens for applications/users to use to access resources. When it comes to how RBAC and Access Keys are implemented, that’s where the fundamental differences lie. With Access Keys, you have generated static Access Key ID and Secret Key ID to be used by the application(s). These keys are either injected into the application environment during setup and can be retrieved by the application on boot, or can be fetched during the runtime of the application from a secret store. Due to the nature of the implementation, when rotating access keys, it is common to restart the application after creating new keys. RBAC roles can be attached to software entities. Once the role is attached to the entity, the entity will be able to access the resources defined by the role. As the role is attached to the software entity, there are no keys to be rotated.
Access Keys are usable by anyone who has the values. Leaking of these sensitive secrets can have financial implications, unauthorized access, data breaches, and much more. As these keys are static and humans make mistakes, unfortunately, there have been countless situations where engineers have used access keys to develop software and accidentally committed the keys to source control. Exposure of these secrets to anyone outside the scope of the application poses a security risk. Should a bad actor discover these keys, they might be able to access systems intended for the target application. There have been thousands of secrets discovered in source control repositories like Github. The longer these keys go undetected, the risk of compromised secrets increases. That’s one reason periodic rotation of access keys is a proactive measure. As a matter of fact, up to 50% of access keys are not rotated periodically.
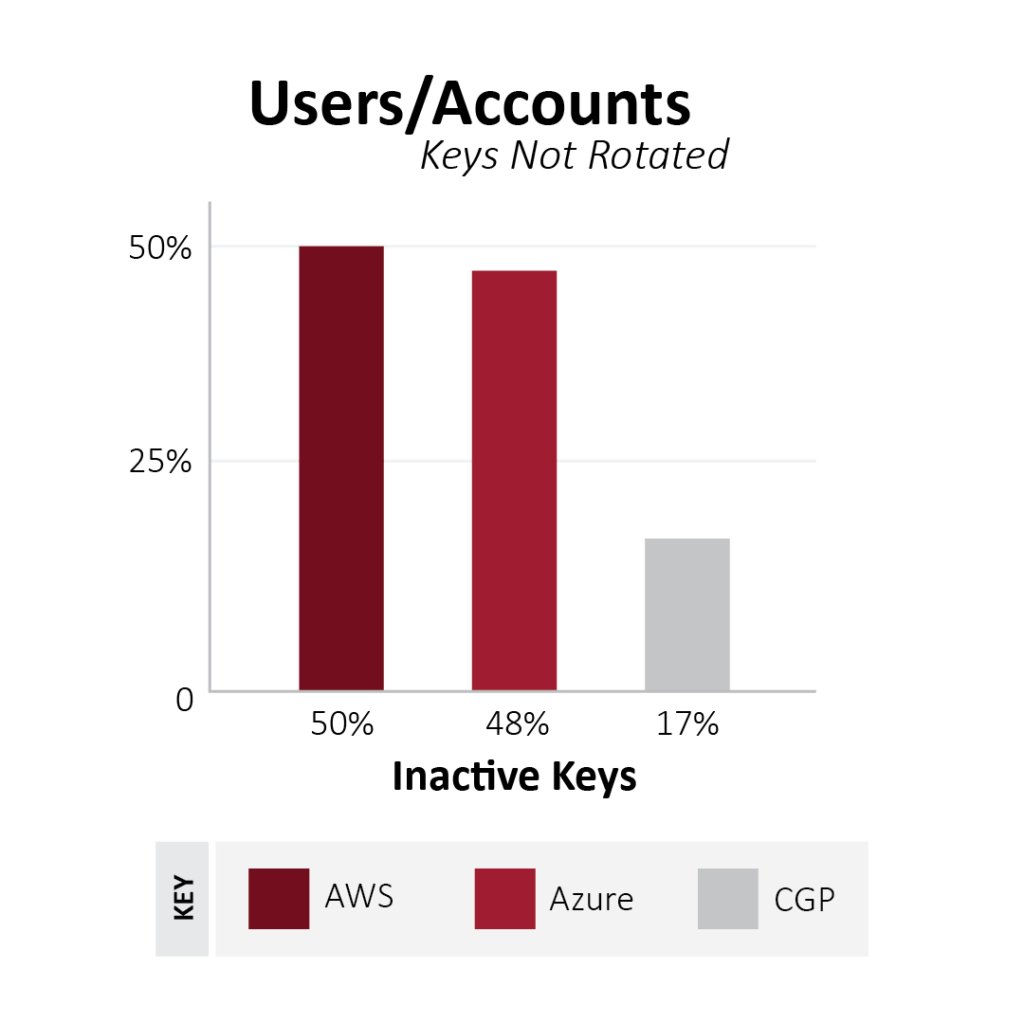
Image Reference
RBAC is directly attached to the entities and does not have static keys, so it inherently does not need a secret rotation cadence. Depending on the software deployment architecture, you can attach the roles to the application as granularly as you like. For virtual servers like EC2, you can attach the roles to the instance itself. For Kubernetes clusters, you can attach IAM roles to Kubernetes Service Accounts through RoleBindings and OIDC (OpenID Connect). RBACs attachment to the software entities prevents misuse by unauthorized parties.
Federal organizations have unique security requirements and compliance regulations that necessitate strict access control measures. By adopting RBAC, these organizations can ensure that only authorized personnel can access sensitive data and resources. RBAC allows for creating roles based on job functions, making it easier to manage access rights across large organizations with complex hierarchies.
When implementing RBAC in federal organizations, it is essential to consider the following best practices:
- Conduct a thorough analysis of job functions and access requirements to define roles accurately.
- Assign roles based on the principle of least privilege, granting only the minimum access rights necessary for individuals to perform their duties.
- Regularly review and update roles to ensure they align with changing organizational requirements and personnel changes.
- Implement a robust audit trail to monitor and log all access attempts and activities associated with each role.
- Provide comprehensive training to employees on RBAC policies and their responsibilities in maintaining the security of the organization’s resources.
By adopting RBAC, federal organizations can reap several benefits, including:
- Enhanced security: RBAC ensures that access to sensitive data and resources is strictly controlled, reducing the risk of unauthorized access and data breaches.
- Improved compliance: RBAC helps federal organizations meet regulatory requirements, such as FISMA and NIST, by providing a framework for managing access control.
- Increased efficiency: With RBAC, access management becomes more streamlined, reducing the administrative overhead associated with managing individual access key permissions.
- Better scalability: As federal organizations grow and evolve, RBAC allows for the easy addition of new roles and the modification of existing ones, ensuring that access control remains effective and efficient.
In conclusion, RBAC offers a more secure and efficient alternative to access keys for federal organizations looking to secure their cloud resources. By implementing RBAC, organizations can mitigate the risks associated with static access keys, such as accidental exposure and the need for frequent rotation. RBAC provides granular access control, allowing organizations to assign roles based on job functions and adhere to the principle of least privilege. By adopting RBAC best practices and leveraging its benefits, federal organizations can enhance their security posture, improve compliance, and streamline access management processes.
References
The 2020 State of Cloud (In)Security
Governance at scale: Enforce permissions and compliance by using policy as code
3 Ways to Reduce the Risk from Misused AWS IAM User Access Keys
Over 100,000 GitHub repos have leaked API or cryptographic keys
What happens when you leak AWS credentials and how AWS minimizes the damage